11.2.1.2 The "Authentication" Tab
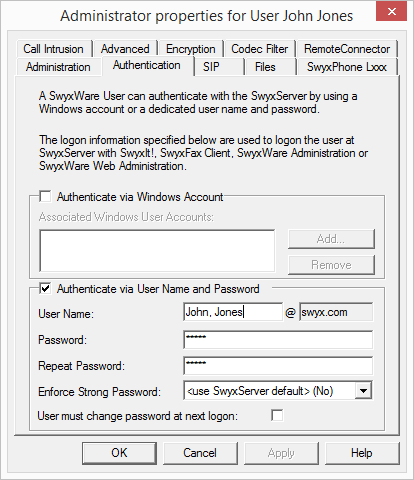
A client's user must authenticate when logging on to SwyxServer. Basically, the following authentication types are available:
You can define for each user which of the three authentication types he is allowed to use.
When logging in, the user is offered two authentication types; even if one or even all of them are not allowed for the user: - Windows account- or Federated authentication - Name/Password authentication Ensure that the user can authenticate using at least one of these options. |
Authentication with Windows user account
Each SwyxWare user can be assigned one or more Windows (domain)user accounts. The SwyxWare user must be logged in using one of these Windows user accounts to be able to use SwyxIt! to place calls. You can add a Windows user by clicking on “Add…” and then making a selection from the list displayed. You can remove a Windows user account from the list by highlighting it and then clicking on “Remove”.
When a user logs in using a Windows user account, the user and SwyxServer need to be within the same domain. |
For the telephony clients within SwyxWare for DataCenter andSwyxON, who are typically not in a domain with the SwyxServer, this authentication is then not possible. |
Federated authentication via identity provider
If your organization uses identity provider services, you can use federated authentication instead of Windows authentication (federated authentication with OAuth 2.0 and OpenID Connect) .
If you enable an identity provider configuration, SwyxServer will offer federated authentication for selection instead of authentication via the Windows user account. Disable all identity provider configurations to reuse Windows authentication. |
Authentication with user name and password
If necessary, enter a user name and password with which a user can log in to SwyxWare Administration and the clients.
The user name must correspond to the UPN format (User Principal Name): User login name +"@" + UPN suffix. You can use the domain name or an alias as the UPN suffix.
Example: john.jones@company.com
You can set the UPN suffix in the server properties, see The "Security" tab.
Currently only the display name can be used to log in to SwyxIt!. The display name can be defined on the “Administration” tab, see User Information. |
Users configured before V 11.25 do not use UPN. To enable these users to log in via UPN, enter the appropriate UPN for each user. |
The user name is used to create a SIP user ID.
Force complex password:
As an administrator, you can force or deactivate the use of complex passwords as a general rule for SwyxServer in server configuration (The "Security" tab)
In SwyxON , the rule to force the use of complex passwords is preset and cannot be revoked by any administrator. |
This rule can be configured individually for each user.
You can select among the following three options in the "force complex password" option field:
The general settings on the SwyxServer apply for the user. This option is set by default.
Regardless of the SwyxServer configuration, the user must set up a complex password.
The corresponding dialog window with brief instructions is shown to the user when changing the password.
The corresponding dialog window with brief instructions is shown to the user when changing the password.
Regardless of the SwyxServer configuration, the user must set up a simple password.
User must change the password at the next login:
When this checkbox is activated, the corresponding telephony or SwyxWare Administration user can no longer log in to SwyxServer using the current account data, and will have to change the password at the next login.
Regardless of password settings, an attempt to re-enter the current password during password change will be checked by the system and will not be permitted. |
The default setting on this checkbox is deactivated.
If a password is assigned to the user and the server rule "force complex password" is set, then the checkbox is automatically activated. However, you can set this activation back.
After a user has changed the password, the checkbox is deactivated automatically.
This setting can meet the following objectives:
If the "force complex password" rule is activated in server configuration and/or user configuration, then the user will be able to continue to use the current password until the user decides to change the password or until the administrator forces password change. |
If a user receives the account data from an administrator, then the new password will only be known to that user after it is changed.
Last modified date: 09.16.2022