21.1 Encryption within SwyxWare
For the actual media data transfer between two end points, the RTP (Real-Time-Transport Protocol) has previously been used. Within the encryption scenario, an end point can be a SwyxIt!, SwyxPhone, ConferenceMgr, LinkMgr, Gateway or a device from another manufacturer. With SRTP it is now possible to transfer media data encrypted and authenticated. SRTP is based on RTP and encrypts the data stream with the encryption algorithm AES (Advanced Encryption Standard).
To enable secure communication by SRTP, a common key (the so-called "PreSharedKey" (PSK)), must be defined between SwyxServer and the respective end point.
Assignment of the keys (PreSharedKeys) by SwyxServer
SwyxServer distributes a key (PSK) to each end point logging on. End point A is given PSK "A" and end point B PSK "B".
For all end points which use the SwyxWare database (e.g. , SwyxIt!, PhoneMgr, ConferenceMgr, LinkMgr, Gateway), SwyxServer automatically creates and distributes a PreSharedKey. On each successful logon of an end point, another key is generated and distributed encrypted to the end point.
Manual key assignment
Exceptions to the automatic PSK distribution are devices from third party manufacturers. The key is not automatically assigned to these by SwyxServer. In such cases the key must be stored manually in the device (e.g. via a web interface). Furthermore, it must be configured in the properties of the user who uses this device. See also The "Encryption" Tab.
The keys for a SwyxLink trunk and a SIP link must also be created manually. For a SwyxLink trunk this must be set correspondingly on both SwyxServer sides; for a SIP link, on the SwyxServer side and on the provider side.
The subsequent exchange of keys by MIKEY and the SRTP connection proceed in exactly the same way for the end points which are given a key manually as for the end points which receive a PSK automatically.
Exchange of keys by MIKEY
generates a session key SK (random key), encrypts this with PSK "A" and sends it to SwyxServer. | decodes SK with PSK "A" and encrypts SK once again with PSK "B". It then sends SK encrypted with PSK "B" to end point B. | decodes SK with PSK "B". |
The end point from which the call is outgoing (here end point A) generates a session key (SK). The secure exchange of the session key is ensured by the protocol MIKEY (Multimedia Internet KEYing). This session key is used by SRTP to encrypt the data stream.
Connection by SRTP
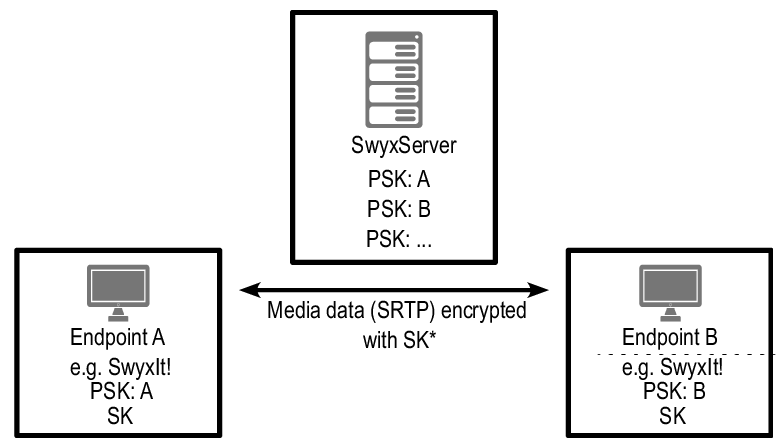
The media data is encrypted with SRTP. This means that calls can no longer be listened to or recorded..
Encryption is dependent on settings of the end points
Whether a call is established, and whether it is correspondingly encrypted from end point to end point (e. g. from SwyxIt! to SwyxIt!), is ultimately dependent on the encryption settings within the user properties:

*It is assumed that the end point supports encryption.
Last modified date: 01/24/2024